How does vulnerability assessment work
Vulnerabilities are security flaws or loopholes that exist in any software. If exploited, these vulnerabilities allows attackers unauthorised access to sensitive or personal information, generally causing havoc by putting your computer at risk, or further multiply into large scale security breached that might incur financial losses or major data leaks in the organisation.
Vulnerability Assessment is a feature of Cloud AV that automatically scans your installed applications to inspect the endpoints and to detect and display a detailed list of the software with their vulnerabilities.
Hence, the most important part of securing a safe environment is to be informed of vulnerabilities always, after which you can decide how you prefer to remediate them. You can avoid these disruptions caused by exploiting vulnerabilities by always remediating them as they are discovered, or by being generally aware of keeping your software up-to-date.
To assess your computer’s vulnerabilities
-
Double-click the Cloud AV icon in the System Tray.
-
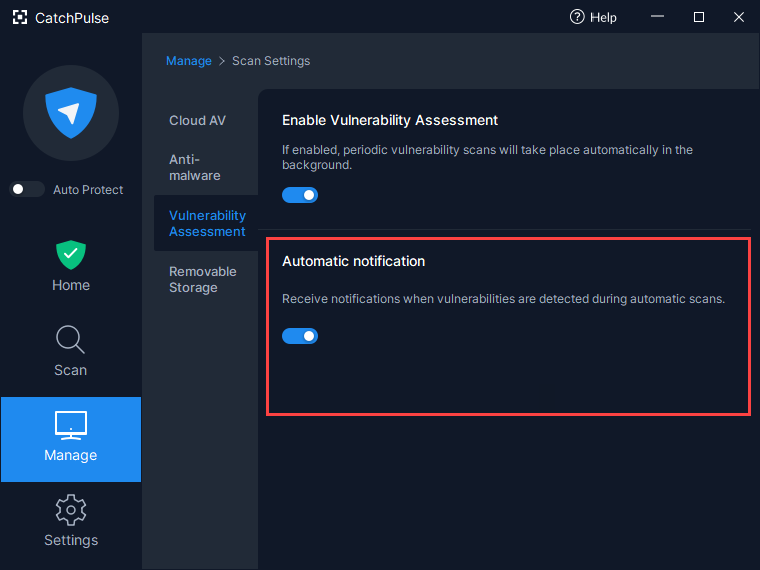
ln Cloud AV Main screen, click Manage → Scan Settings
- Click Vulnerability Assessment.
-
After running Vulnerability Assessment, a list of vulnerable applications displays.
Click Details to view the details related its individual vulnerabilities.
-
While CatchPulse advises on possible remediation actions for these vulnerabilities (e.g. uninstalling the application, updating the application), the remediation itself is a manual process.
-
(Optional) When turned ON, the Automatic Check setting automatically runs Vulnerability Assessment periodically (typically every day, or whenever the machine boots up). When vulnerabilities are detected during the automatic check, CatchPulse prompts to inform you that vulnerabilities are detected.
Support and feedback
Should you encounter any issues using CatchPulse with any of the mentioned or missed requirements above, you can write to us at docs@secureage.com.
This page was last updated: January 20, 2026