Manage CatchPulse Untrusted Items
Note: This section applies to users who have a valid CatchPulse Pro license
You can view all the untrusted files which are installed in the machine or device. Items that are blocked (untrusted status) by CatchPulse will be reflected on this page.
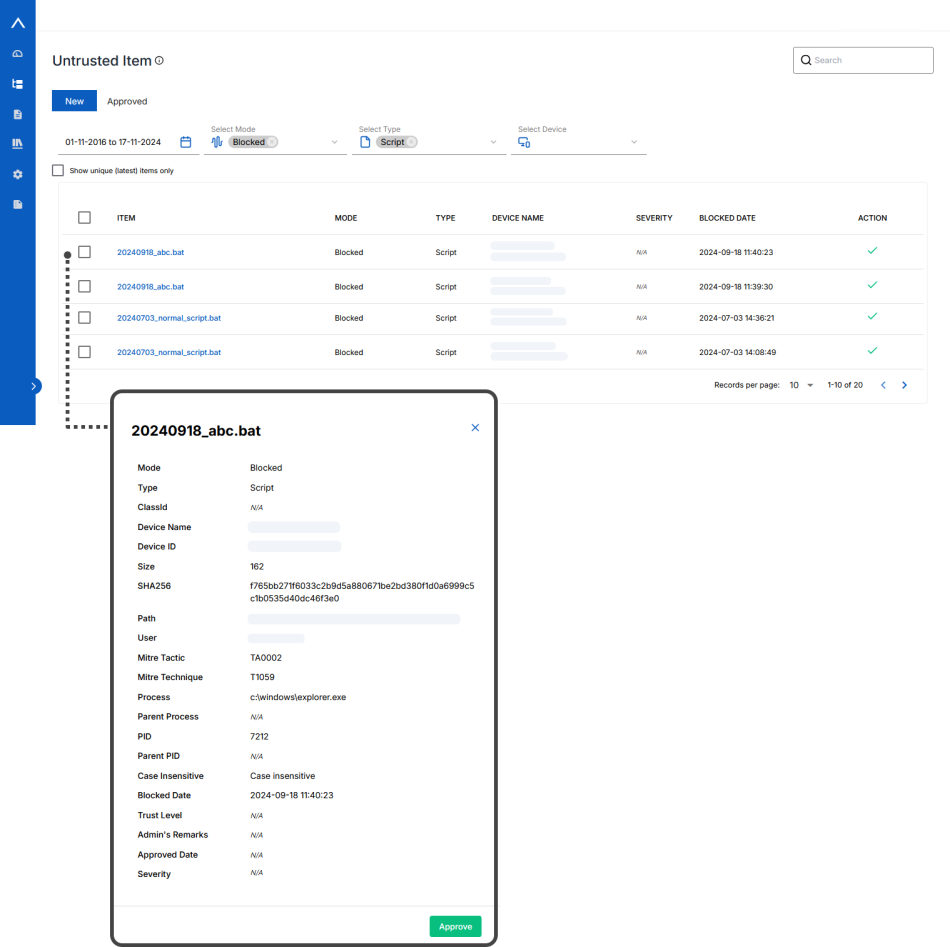
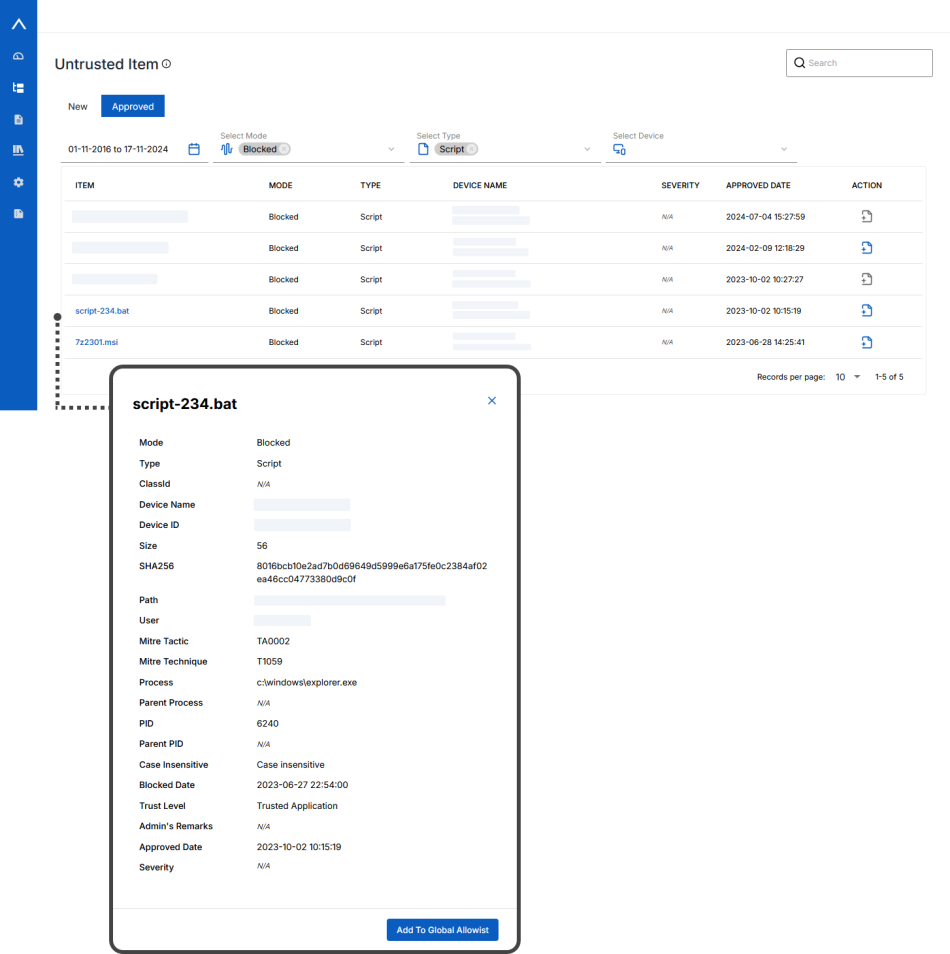
View Untrusted Item Details
To view untrusted item details
-
On the main navigation bar, go to .
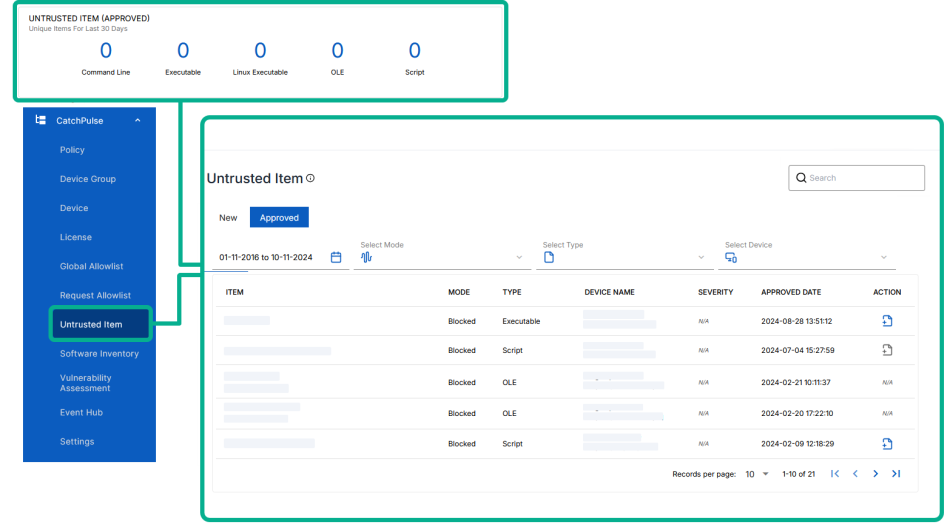
-
Select an untrusted item.
The information pane on the right indicates more details about the device.
Untrusted files are applications or items within your computer or device that your security team has not approved or authorized. The trustworthiness of these items is determined by the Application Allowlisting feature within CatchPulse, which tags a trust level to each application and executable so that untrusted or not allowlisted applications will not be able to run on your computer. This minimizes the chances of authorized malware damaging the user's system.
In Application Allowlisting, there are three levels of trust for applications, summarized in the table below:
| Trust Level | Description |
|---|---|
| Untrusted |
The application is not allowed to be executed at all. Any files that are created by this application will not be trusted as well. |
| Trusted Application |
The application is allowed to be executed, but all the files that are created by a Trusted Application will be Not Trusted. Example: explorer.exe is a Trusted Application, but all files that are created by explorer.exe will not be automatically trusted. Using explorer.exe, a user may copy any files from anywhere, and all of these files cannot be automatically set as Trusted Application without the administrator approval. Similar situations apply for applications such as Internet Browser, FTP, e-mail client, etc. For better security measurement, most of applications should fall under this category. |
| Trusted Installer |
Installer, uninstaller, and updater applications usually fall into this category. A Trusted Installer is allowed to be executed, and all files that are created or rename by a Trusted Installer will be automatically set as Trusted Application. There is a special exception for update process. When a Trusted Installer found that the file already exists, and the trust level has been set to be Trusted Installer, Trusted Installer will not downgrade the file as a Trusted Application; instead it will keep the trust level as it is. |
More on setting trust levels of file/ applications in CatchPulse endpoint
Support and feedback
Should you encounter any issues using the SecureAge Central with any of the mentioned or missed requirements above, you can always write to us a docs@secureage.com.
This page was last updated: March 21, 2025
