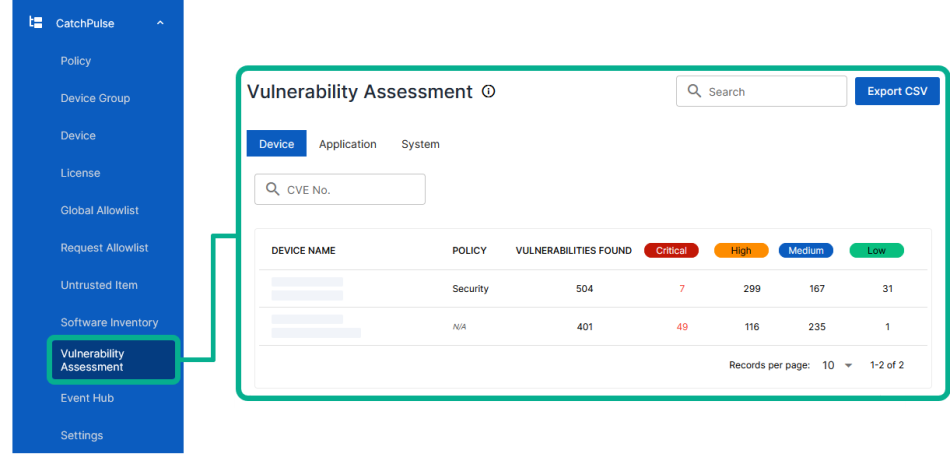
Vulnerability Assessment
Vulnerabilities refer to security flaws or loopholes present in any software. If these vulnerabilities get exploited, attackers can gain unauthorized access to sensitive or personal information, thus putting your computer at risk or leading to large-scale security breaches that can cause financial losses or major data leaks.
Vulnerability Assessment is a feature of Cloud AV that automatically scans your installed applications to inspect the endpoints and detect and display a detailed list of the software with their vulnerabilities.
Therefore, staying informed about vulnerabilities is crucial for maintaining a safe environment. Once you are aware of vulnerabilities, you can decide how to remediate them. You can avoid the disruptions caused by exploiting vulnerabilities by either remediating them as soon as they are discovered or keeping your software up-to-date.
Checking Common Vulnerabilities and Exposures (CVEs)
To check Common Vulnerabilities and Exposures (CVEs)
-
On the main navigation bar, go to .
-
Choose the Device, Application or System tab.
-
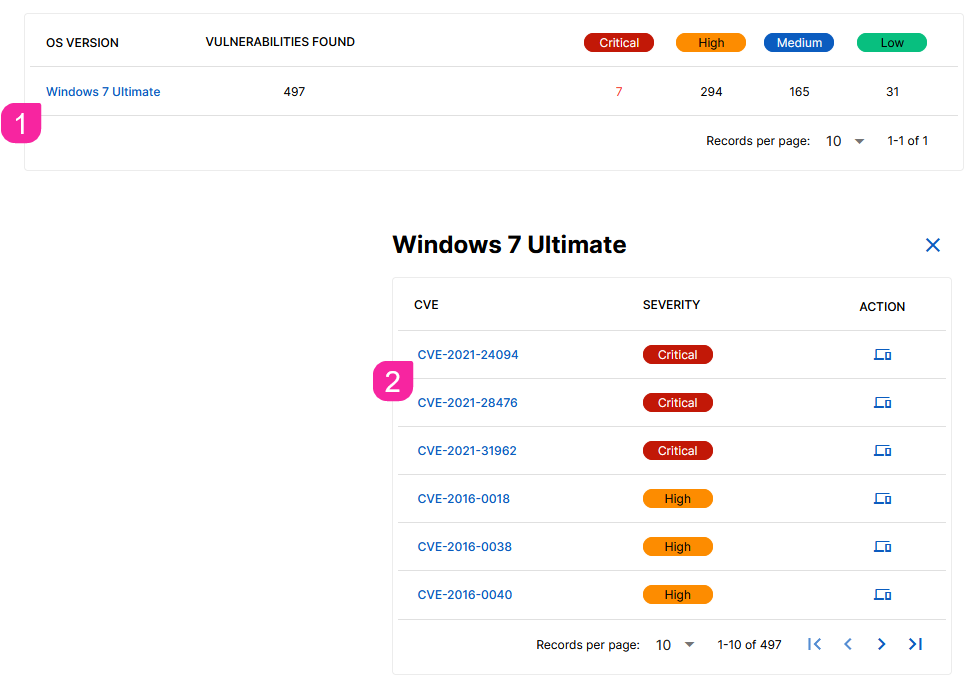
Select a Device, Application or System.
-
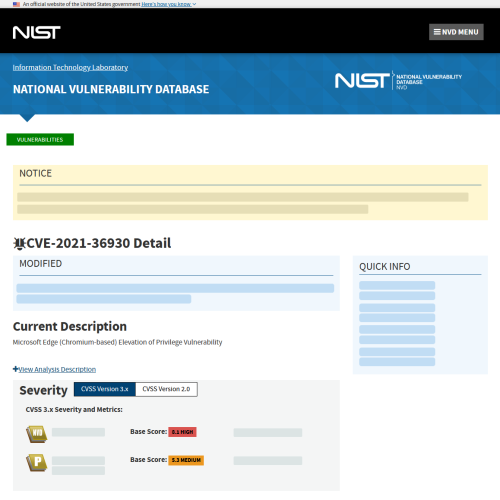
Select a CVE identification number, and you are presented with the details of the relevant CVEs such as their description, severity and Common Vulnerability Scoring System (CVSS).
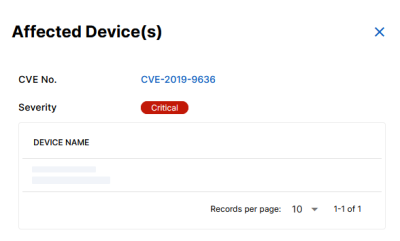
Show the Affected Devices
To show Affected Devices
-
On the main navigation bar, go to .

-
Choose the Device, Application or System tab.
-
Select a Device, Application or System.
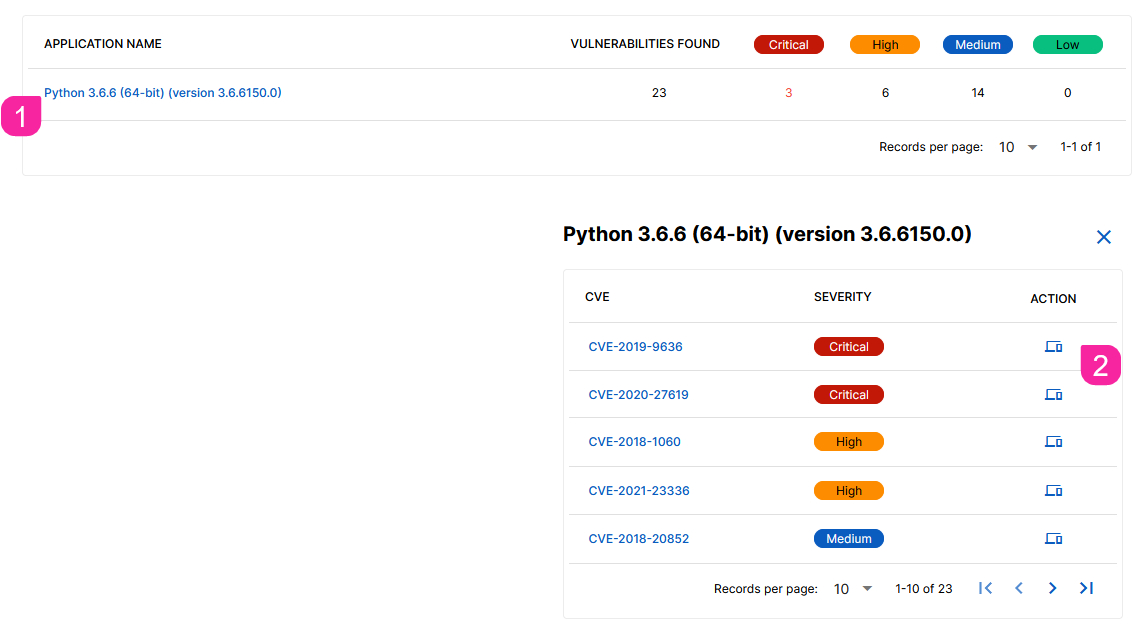
You are presented with a list of devices affected by the vulnerability assessment.
Support and feedback
Should you encounter any issues using the SecureAge Central with any of the mentioned or missed requirements above, you can always write to us a docs@secureage.com.
This page was last updated: March 21, 2025
