Create a SecureAPlus policy
Only users with Pro licenses can create a SecureAPlus Policy.
A SecureAPlus Policy is a collection of pre-defined SecureAPlus settings that can be easily deployed and imposed to attached SecureAPlus Pro devices with the Policy Add-on feature.
To create a SecureAPlus Policy in your SecureAPlus Account Portal.
-
Log in to your SecureAPlus Portal.
-
On the SecureAPlus Account Portal Summary page, click on Policy → Add Policy.
-
Begin pre-defining a collection of customized settings for a linked SecureAPlus installation.
Note: Inherit Default toggle and drop-down choices means that the pre-defined settings that as determined by the SecureAPlus team (i.e. software default settings) will be taken into account in addition to anything that the user has set.
Client Settings tab
1
In the Policy Info sub-tab, enter a name for the policy. Make sure to use a name that will help in identifying this policy from the default and other policies (i.e. name of a department, company user type, privilege level, etc).
After naming the policy, you may begin pre-defining a collection of customized settings for a linked SecureAPlus installation.
2
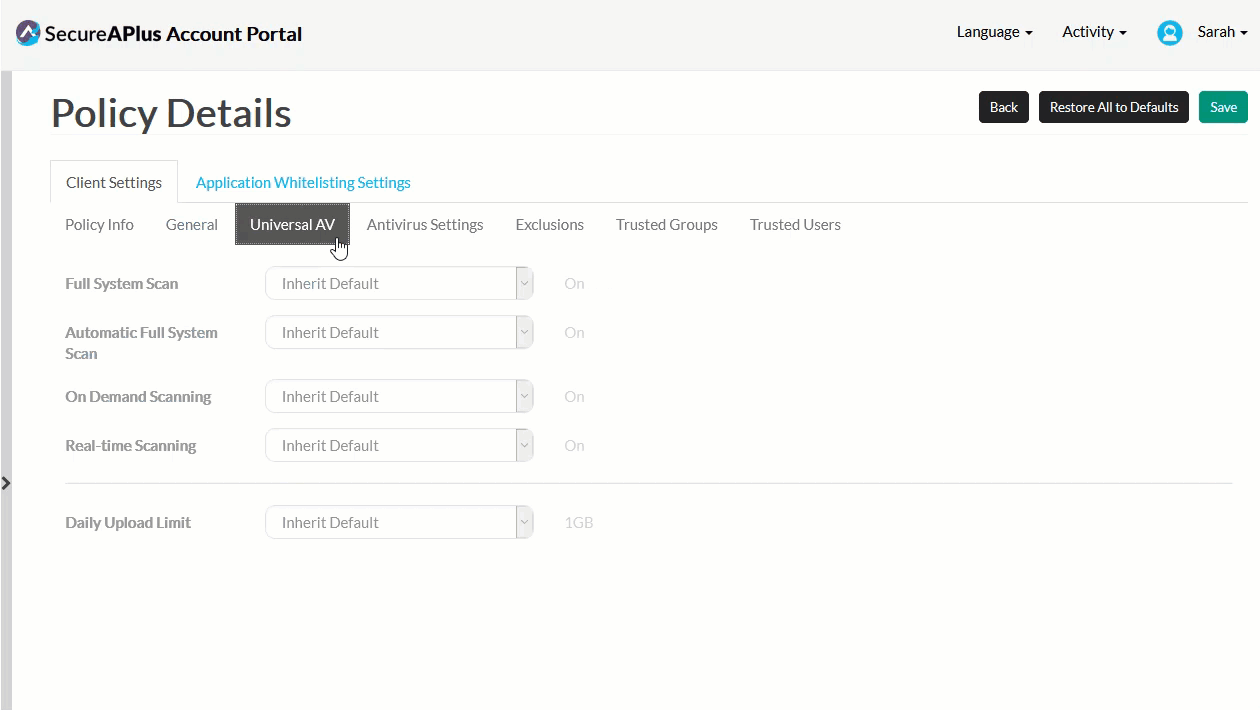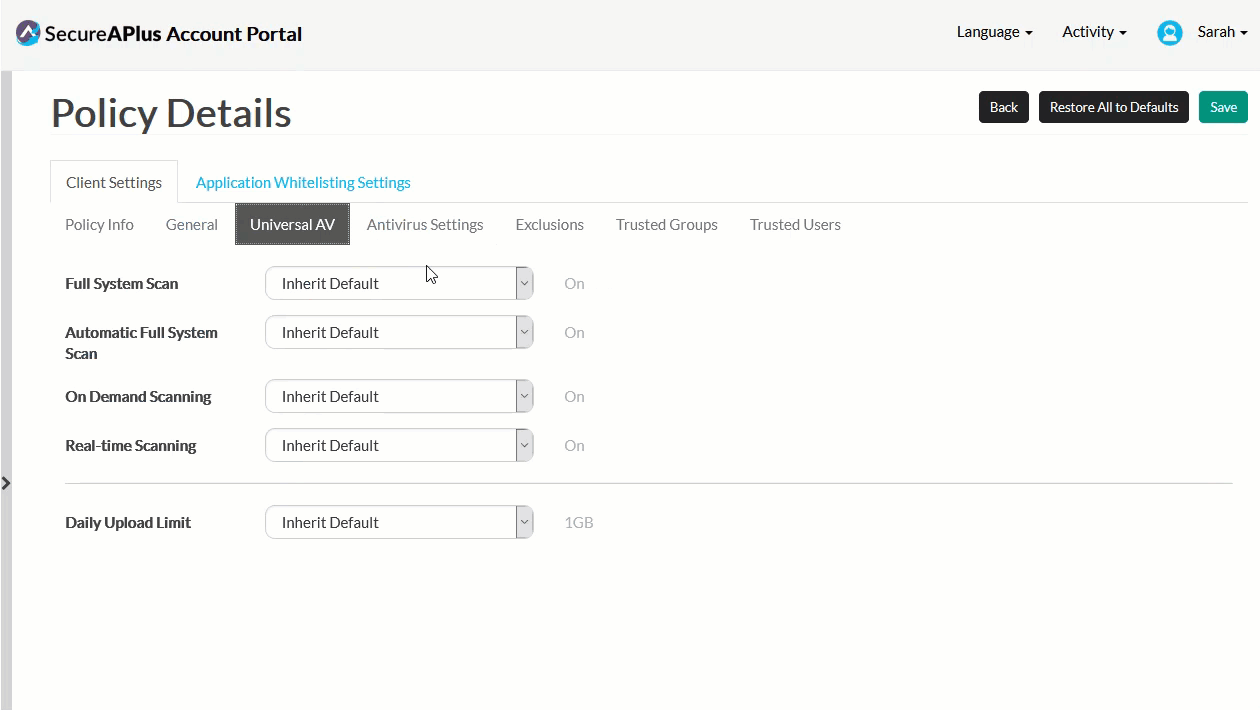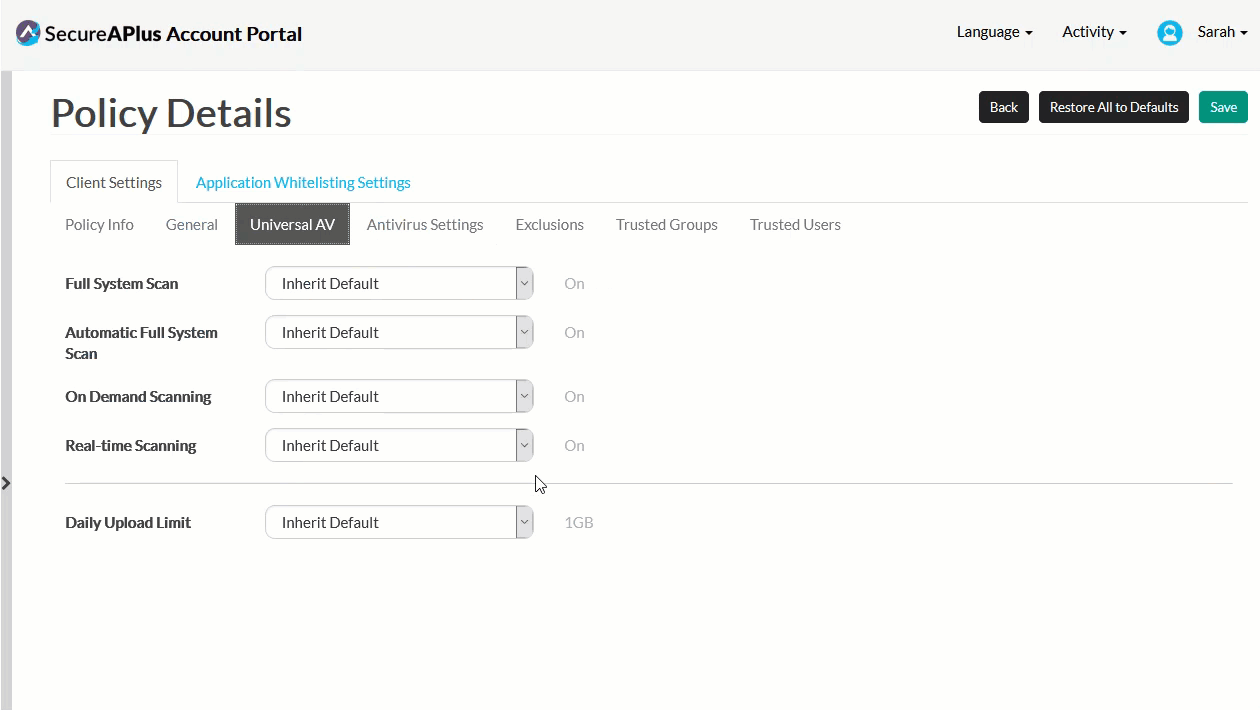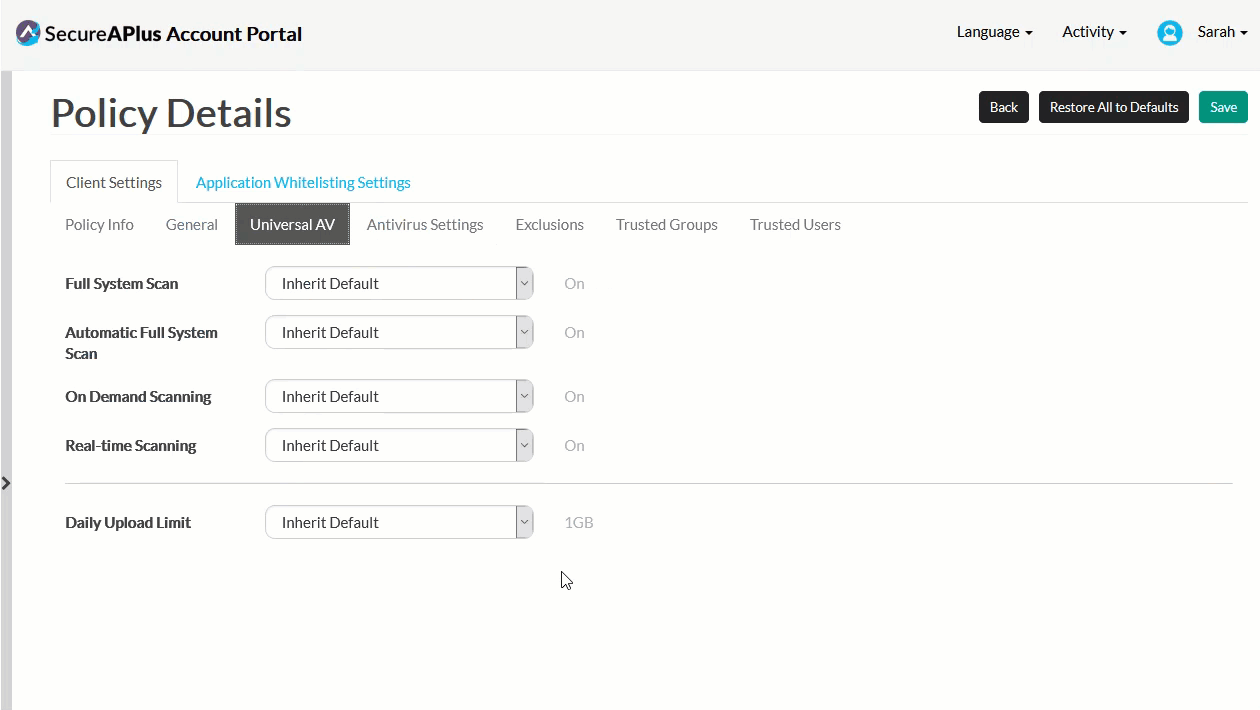
In the Universal AV sub-tab, specify Full System Scan, Automatic Full System Scan, On Demand Scanning, Real-time Scanning and Daily Upload Limit settings or inherit the default setting for each.
3
In the Antivirus sub-tab, specify the preferred APEX Sensitivity, Antivirus, and Real-Time Scanning settings or inherit the default setting for each.
4
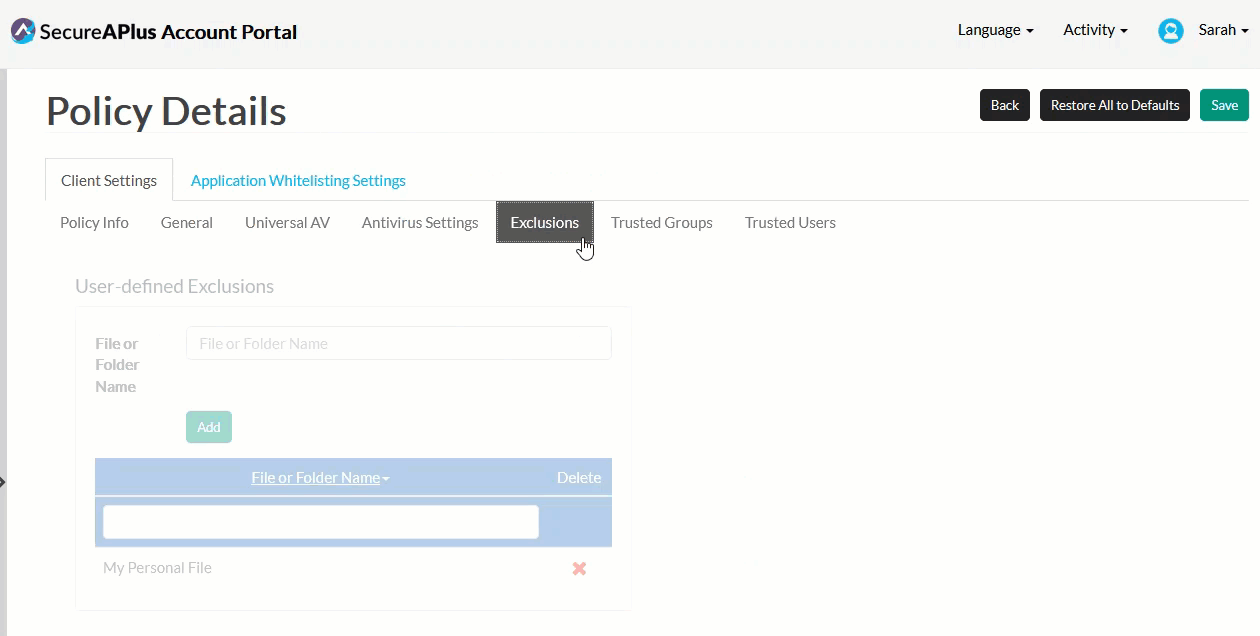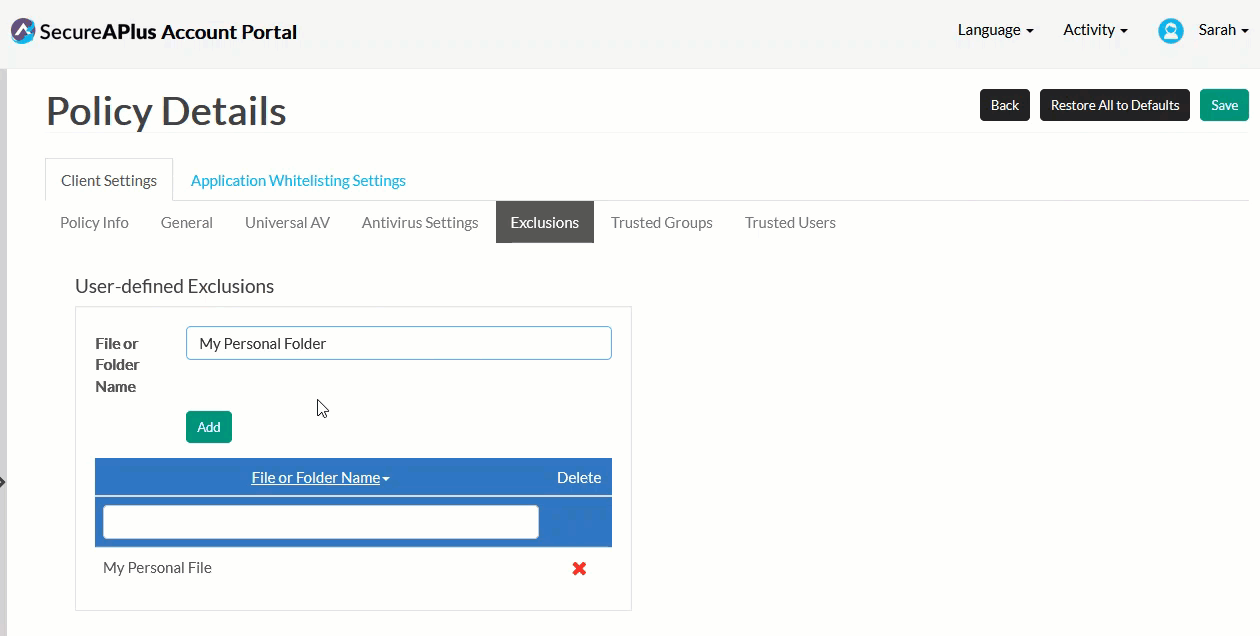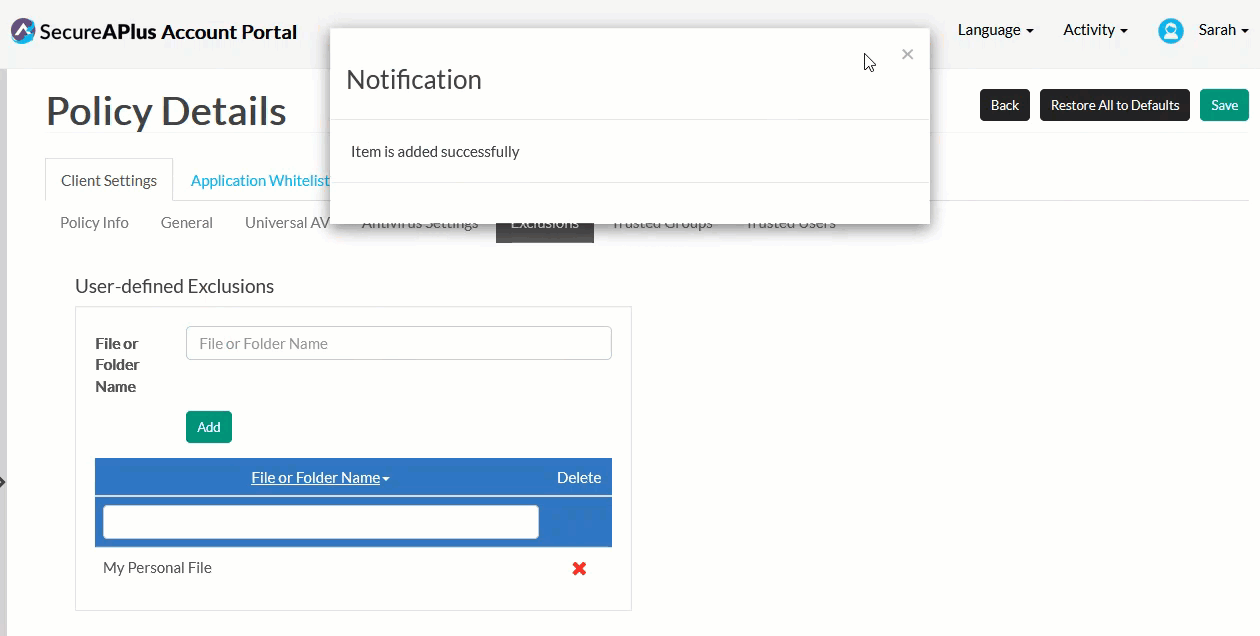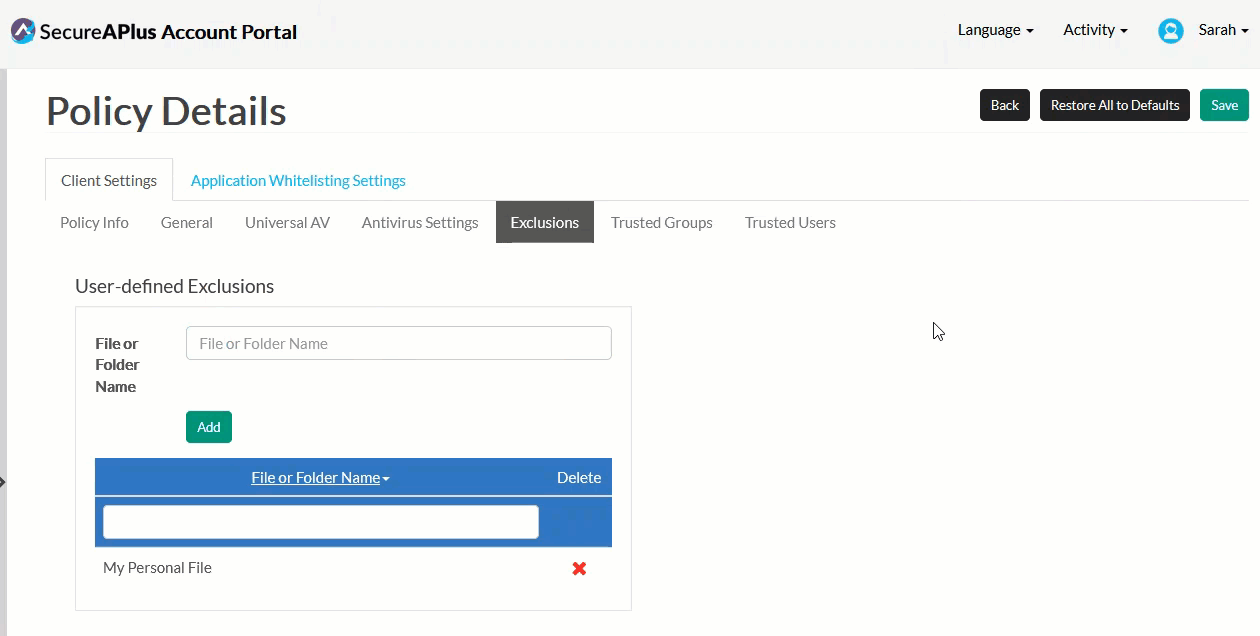
In the Exclusion sub-tab, specify the files or folders to be excluded from scanning.
-
Type in the name of the file or folder you want to be excluded from scanning and click Add.
-
If you have more that one file and folder to add, repeat Step 1 until you've completed adding all of them into the User-defined Exclusions list.
5
In the Trusted Group sub-tab, specify the Trusted Groups who will have the rights to
-
add new allowlist
-
modify the trust level of each program file
-
run any installation software that is trusted as an installer modify SecureAPlus settings.
To specify the Trusted Groups
-
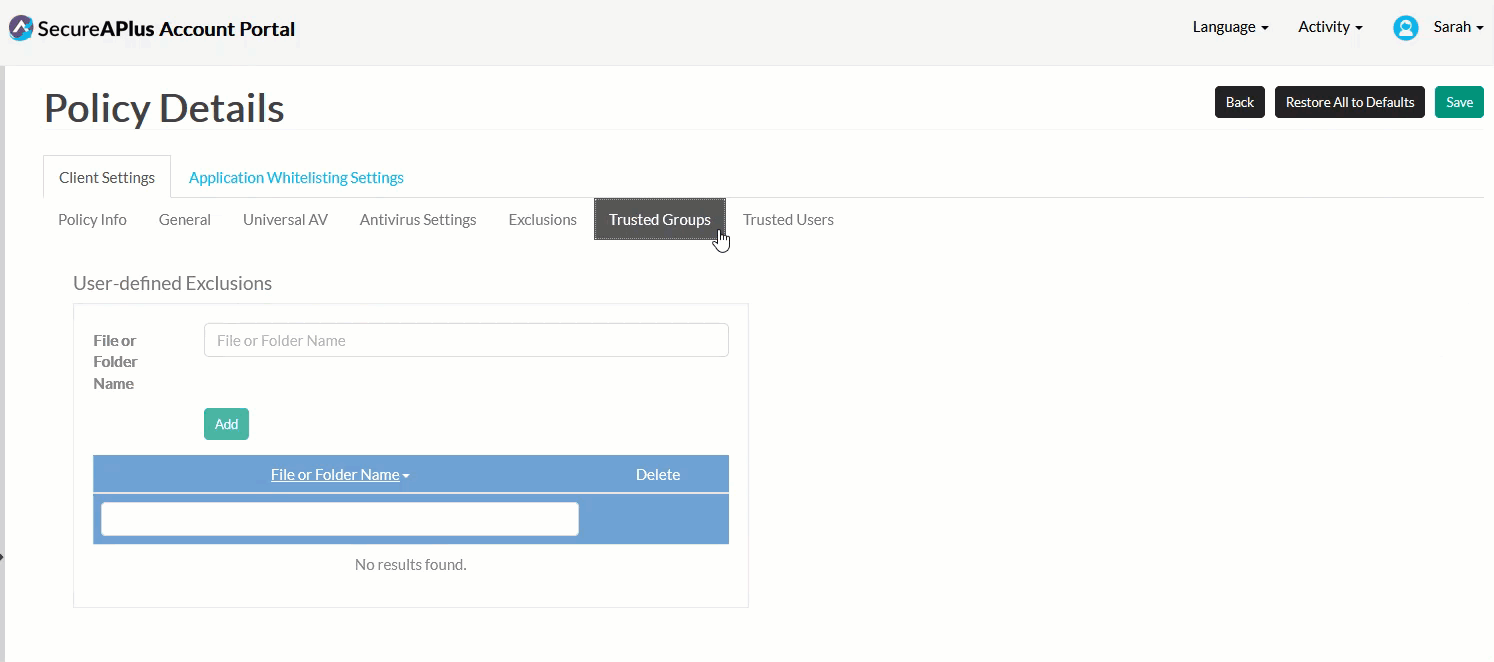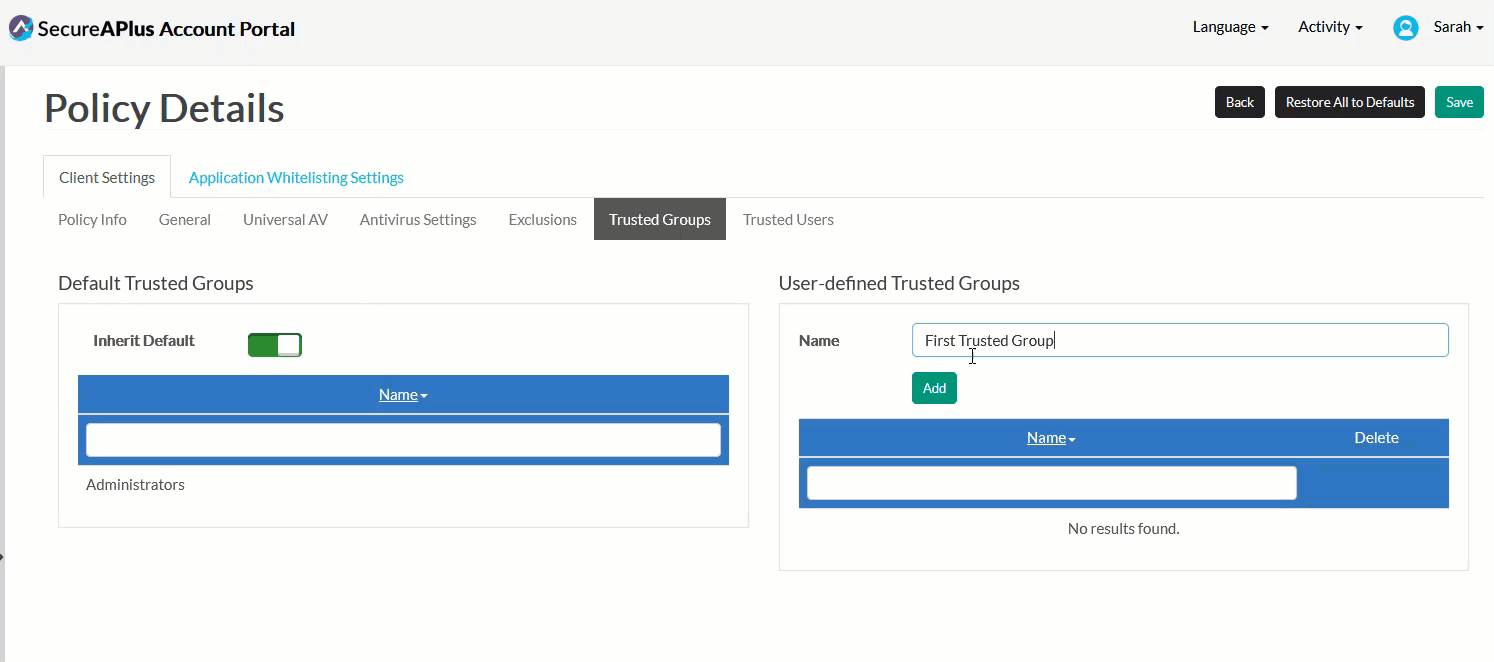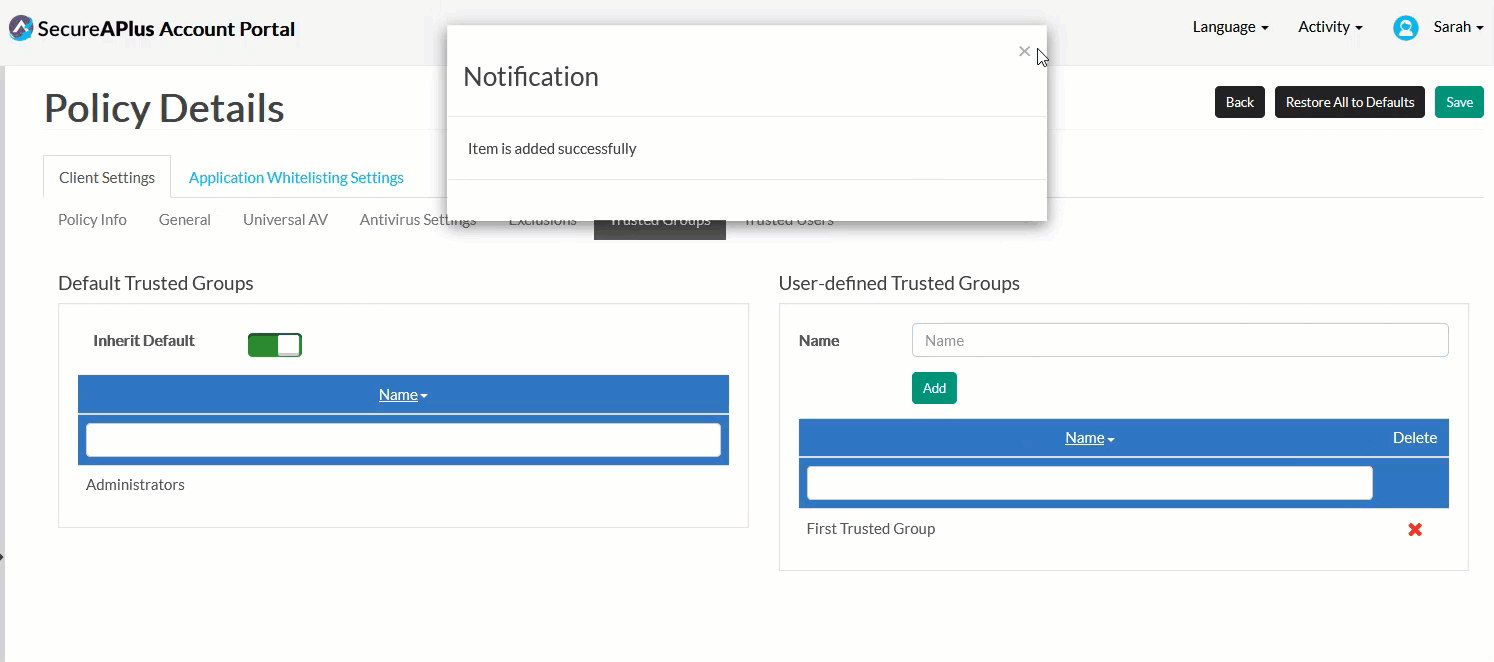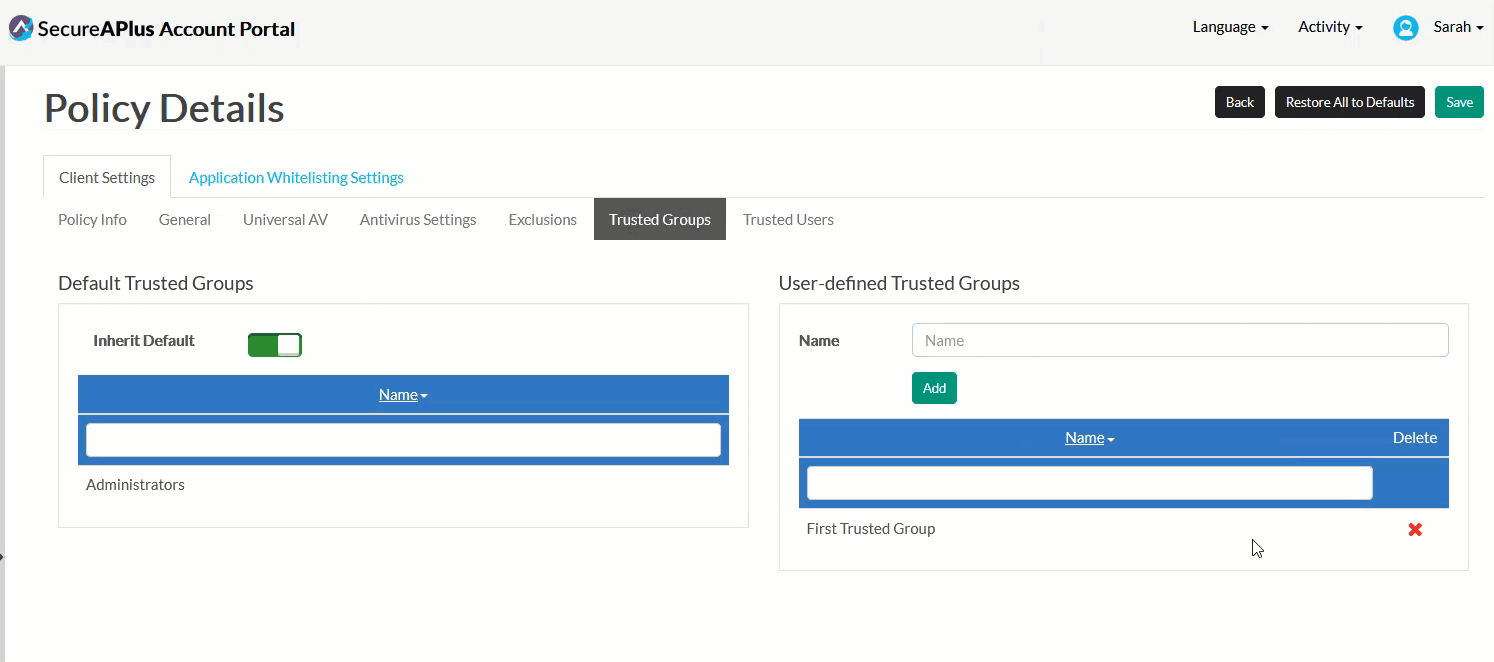
In the Default Trusted Groups box, decide whether you'd like to inherit Default Trusted Groups. If you'd like to disable this setting, toggle the button beside Use Default Trusted Group to off.
-
In the User-defined Trusted Groups box, define your own Trusted Group by typing in the name of the group you'd like to trust in the textbox provided, and click Add.
-
If you have more that one Trusted Group to add, repeat Step 2 until you've completed adding all of them into the User-defined Trusted Groups list.
6
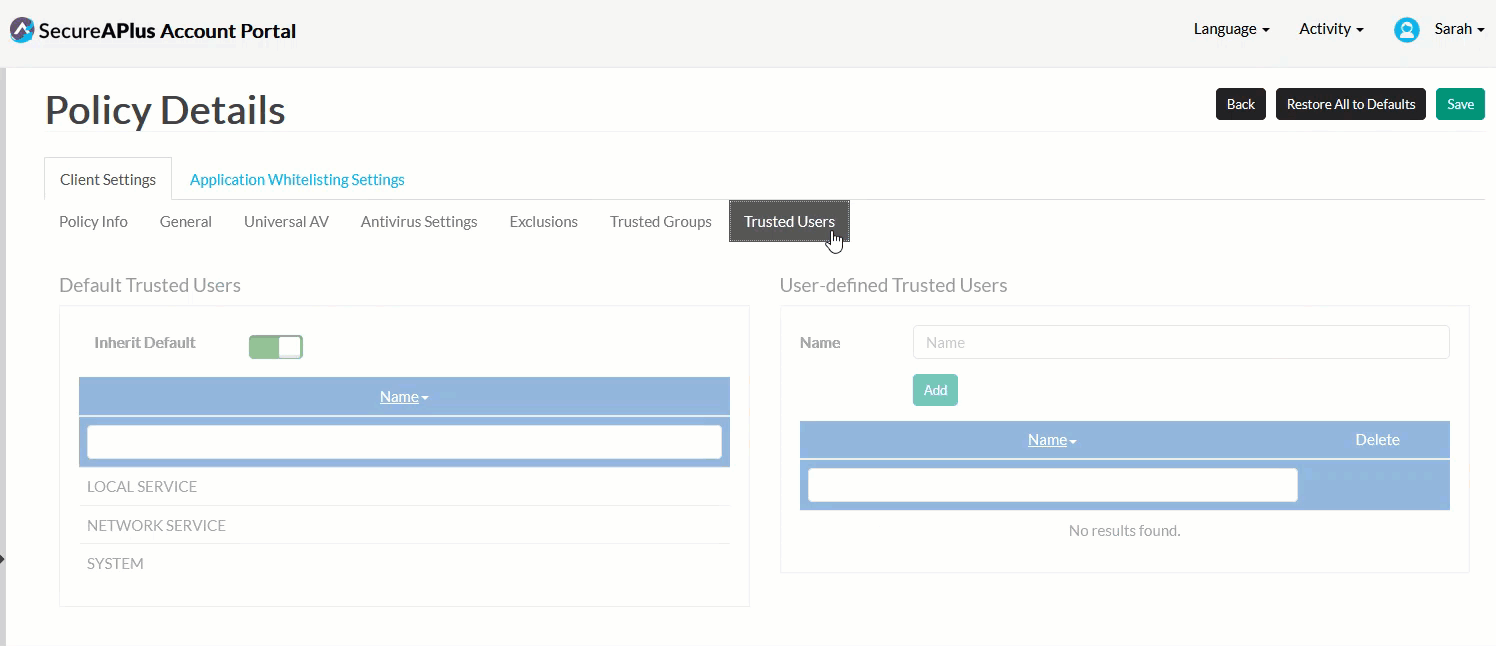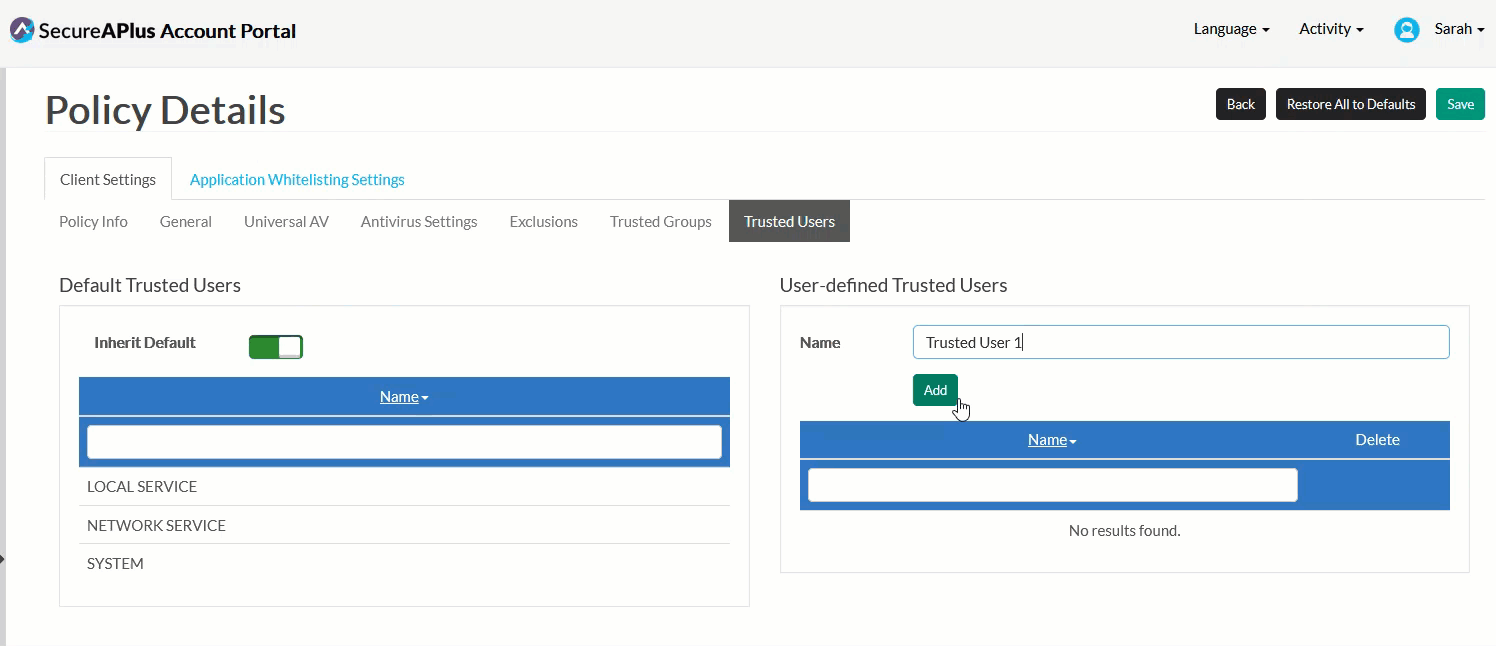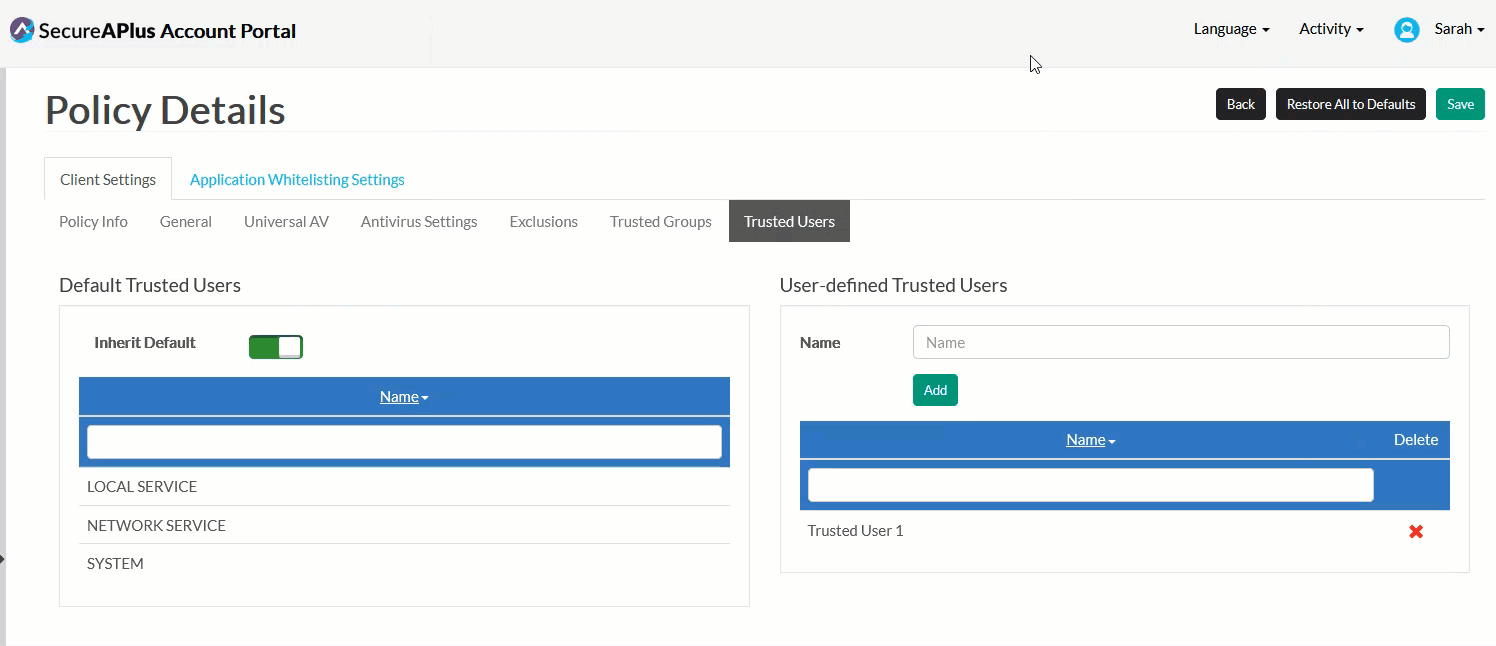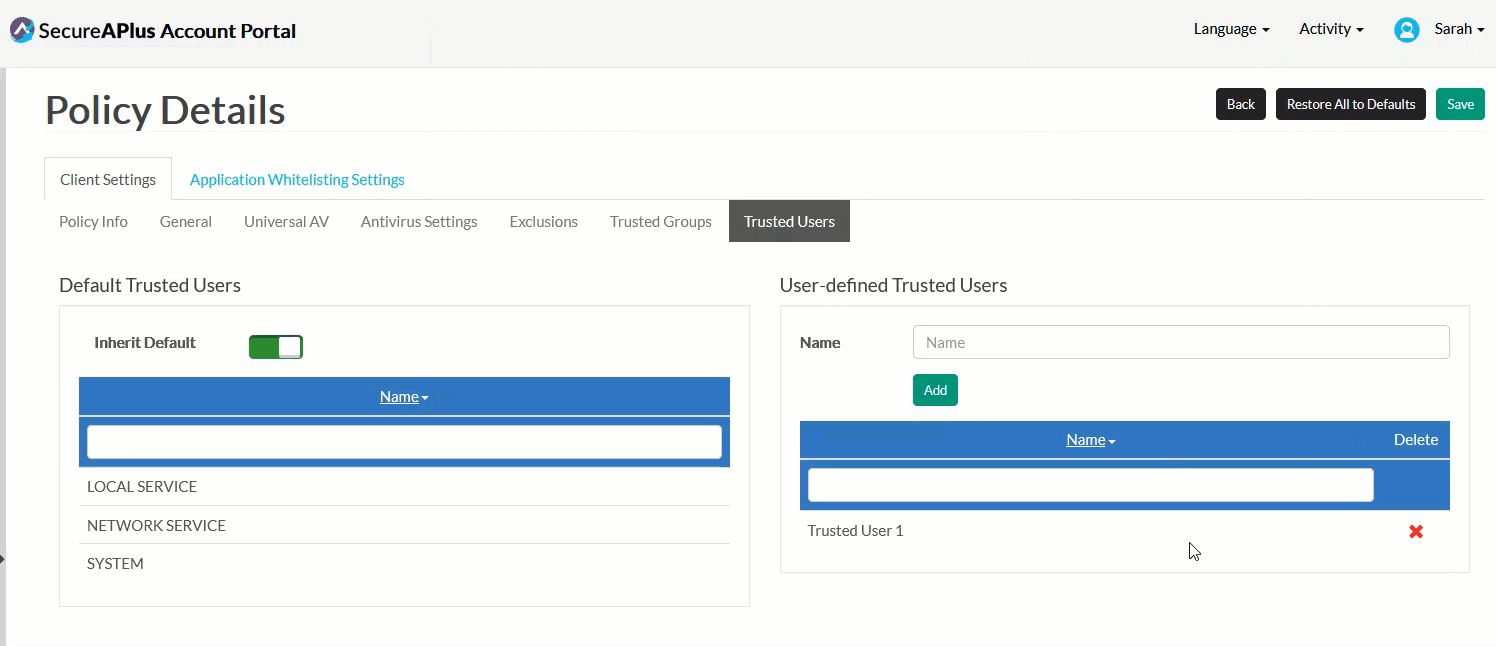
In the Trusted User sub-tab, specify the Trusted Users who will have the rights to
-
add new allowlist
-
modify the trust level of each program file
-
run any installation software that is trusted as an installer
-
modify SecureAPlus settings
To specify the Trusted Users:
-
In the Default Trusted Users box, decide whether you'd like to inherit Default Trusted Users. If you'd like to disable this setting, toggle the button beside Use Default Trusted Group to off.
-
In the User-defined Trusted Users box, define your own Trusted User by typing in the name of the user you'd like to trust in the textbox provided, and click Add.
-
If you have more that one Trusted User to add, repeat Step 2 until you've completed adding all of them into the User-defined Trusted Users list.
Application Allowlisting Settings tab
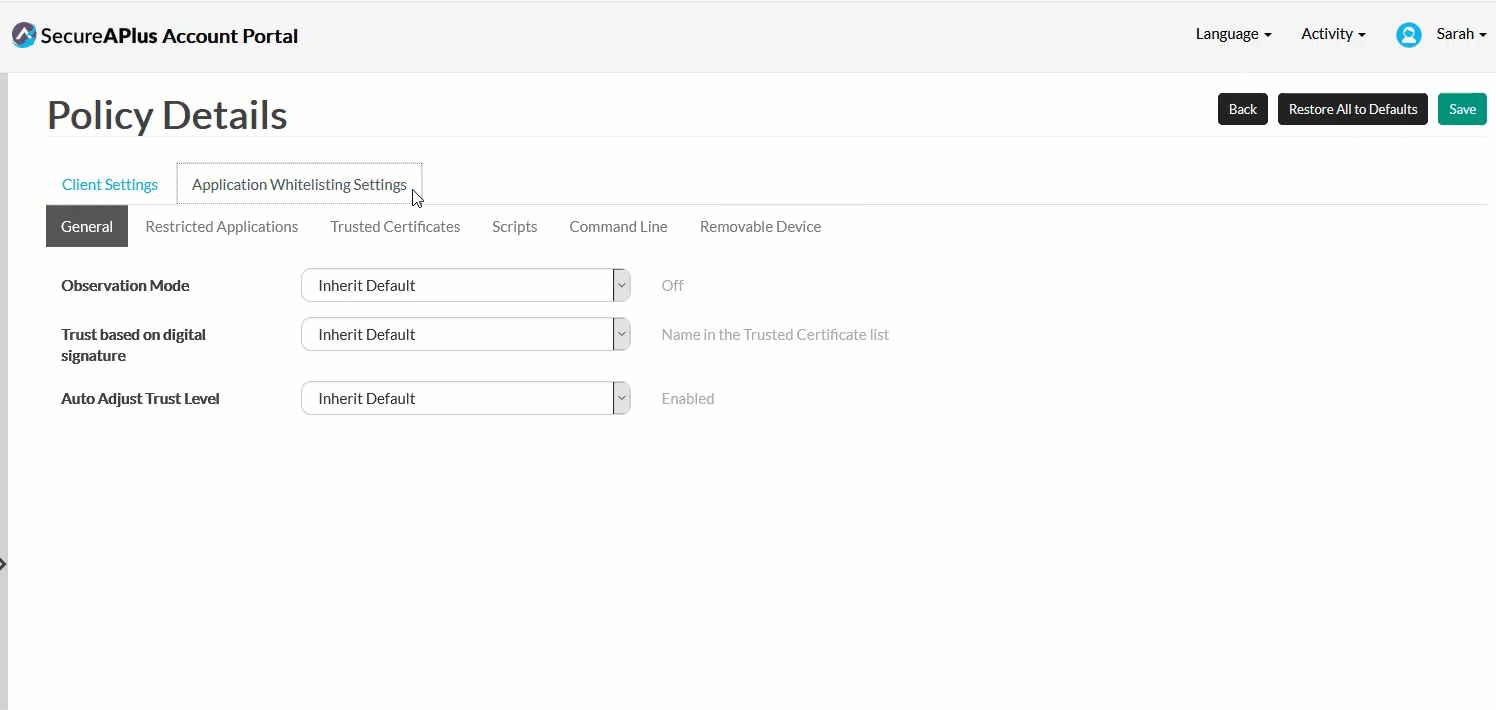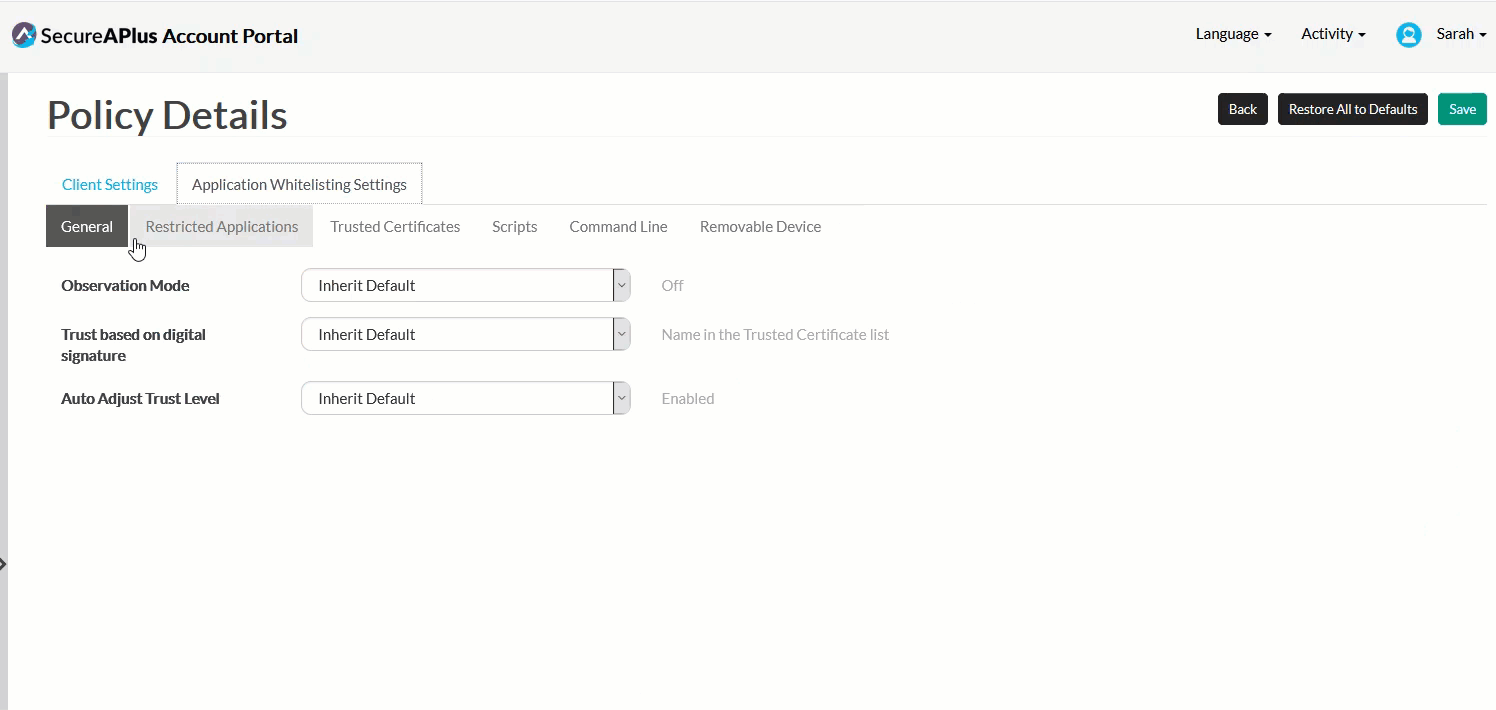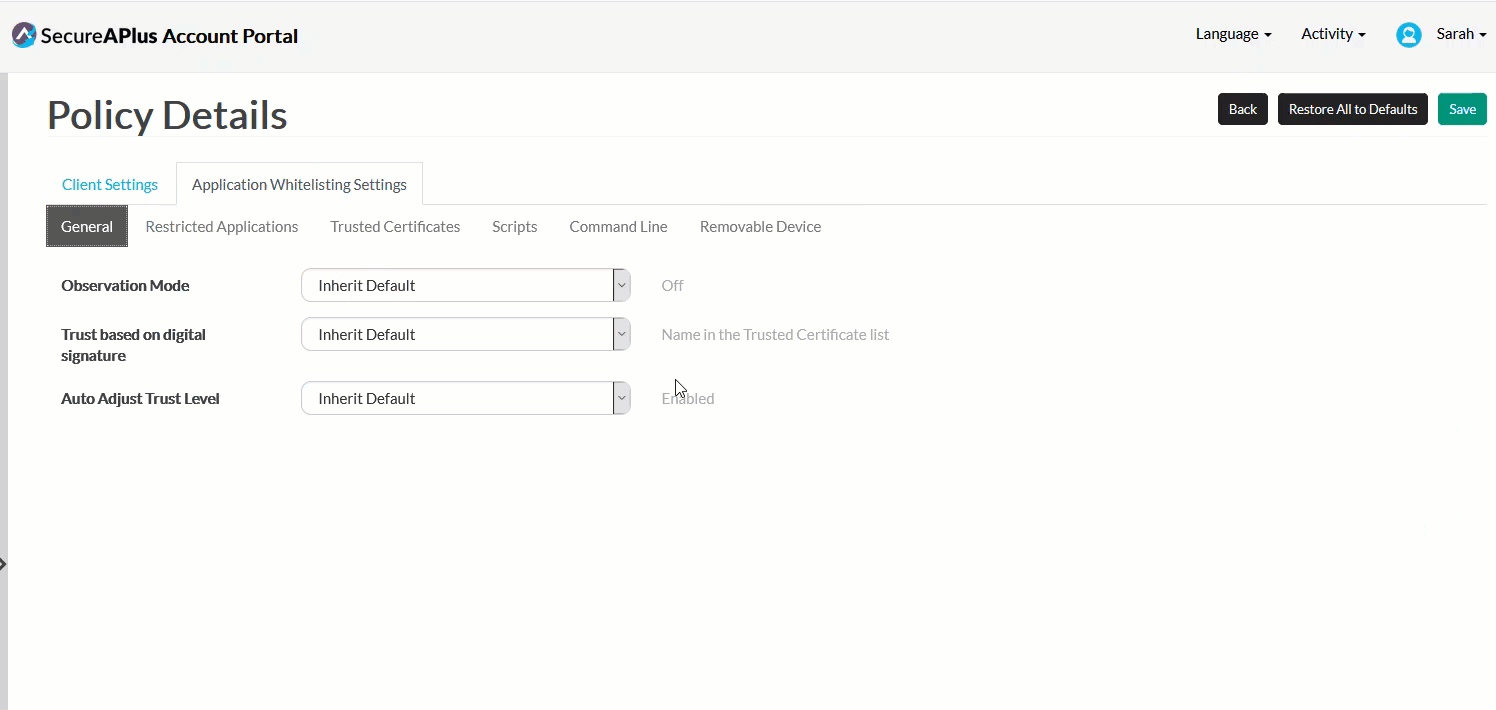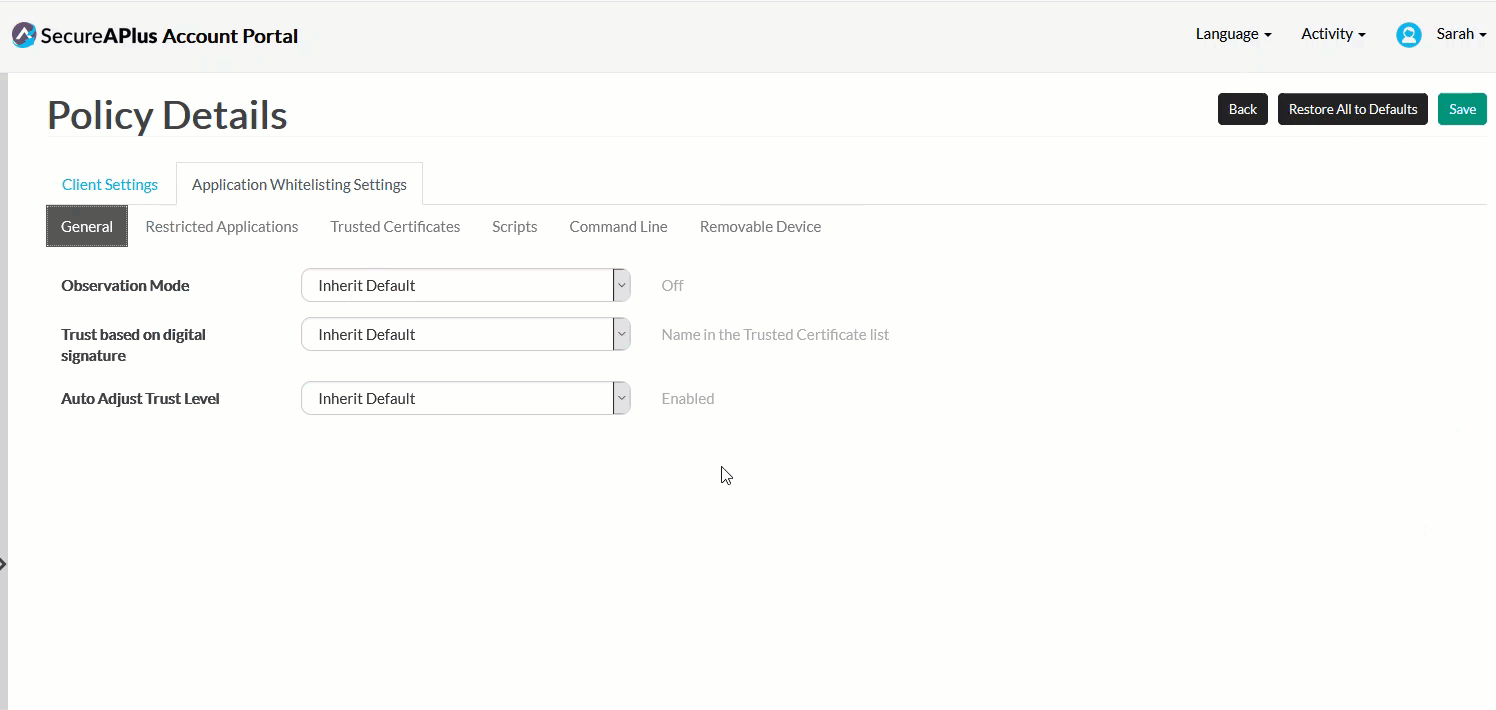
1
In the General sub-tab, specify Observation Mode,Trust based on digital signature, and Auto Adjust Trust Level or inherit the default setting for each.
2
In the Restricted Application sub-tab, you can add an application to a Restricted Applications list, so that it will not automatically bring in other applications that may potentially harm the user’s system.
To add an application to a Restricted Applications list:
-
In the Default Restricted Applications box, decide whether you'd like to inherit Default Restricted Applications. If you'd like to disable this setting, toggle the button beside Use Default Restricted Application to off.
-
In the User-defined Restricted Applications box, define your own Restricted Application by typing in the name of the user you'd like to restrict in the textbox provided, and click Add.
-
If you have more that one restricted application to add, repeat Step 2 until you've completed adding all of them into the User-defined Restricted Applications list.
3
Only applications which have their certificate listed under the Trusted Certificate list will be trusted.
In the Trusted Certificates sub-tab, click here to add trusted certificates into a policy in SecureAPlus Account Portal.
4
In Application Allowlisting, executing a script requires both the script interpreter (which executes the script) and the script file itself to be trusted. The script interpreter will refuse to open any non-trusted file.
If the script has a higher trust level than the script interpreter, the script interpreter trust level will match its trust level to the trust level of the script file. On the other hand, if the script has a lower trust level than the script interpreter, the script interpreter will be running at its own trust level.
To manage Script Interpreters in SecureAPlus Portal Scripts sub-tab:
-
In the Default Scripts box, decide whether you'd like to inherit Default Scripts. If you'd like to disable this setting, toggle the button beside Inherit Default to off.
-
In the User-defined Scripts box, add a User-defined Script by typing in the Interpreter and Extensions in the textbox provided, and click Add.
-
If you have more that one User-defined Script to add, repeat Step 2 until you've completed adding all of them into the User-defined Script list.
5
Command Line Rules extend the allowlisting coverage to file-less attacks that make use of already trusted applications to infect PCs. Such attacks do not exist as a file and can remain undetected by Anti-malware programs and threaten the security of the user’s system.
This advanced feature of SecureAPlus enables users to make additional rules on top of the default ones to increase the overall security of SecureAPlus according to user preference and technical knowledge.
To add more Command Line Rules in SecureAPlus Portal Command Line sub-tab:
-
In the Default Command Line box, decide whether you'd like to inherit Default Command Lines. If you'd like to disable this setting, toggle the button beside Inherit Default to off.
-
In the User-defined Command Line box, add a User-defined Command Line by typing the Process file name without the path and Parameter.
-
Next, select the desired Rules, Case-sensitivity preference and Action, then click Add.
-
If you have more that one User-defined Command Line to add, repeat Step 2 until you've completed adding all of them into the User-defined Command Line list.
6
In the Removable Device, customize how external removable storage devices are treated when inserted or inherit the default setting for each.
Additionally, you can also add a User-defined allowlisted removable storage device in the Removable Device sub-tab.
To add more User-defined allowlisted removable Storage Device in SecureAPlus Portal Removable Device sub-tab:
-
In the User-defined allowlisted removable Storage Device box, add a User-defined allowlisted removable Storage Device by typing the Vendor, Product ID and Serial Number information of the removable Storage Device, then click Add.
-
If you have more that one User-defined allowlisted removable Storage Device to add, repeat Step 1 until you've completed adding all of them into the User-defined allowlisted removable Storage Device.
-
-
Once all settings have been finalized for the policy, click on Save to add this to your My Policy list or implement any of the changes if you were editing an existing listed policy. After creating a policy you can then assign it to SecureAPlus Pro installation linked to your account with the Policy Add-On feature.
Learn more on How to Setup an Installation Managed by SecureAPlus Portal
Support and feedback
Should you encounter any issues using SecureAPlus with any of the mentioned or missed requirements above, you can write to us at docs@secureage.com.
This page was last updated: December 02, 2025