Configuring Command Line Rules Settings in CatchPulse Policy
Command Line Rules extend the allowlisting coverage to file-less attacks that make use of already trusted applications to infect PCs. Such attacks do not exist as a file and can remain undetected by Anti-malware programs and threaten the security of the user's system.
Jump to:
Disabling Default Command Line Rules
Adding multiple rules with varying parameters to the same process
Adding New User-Defined Command Line Rules
What is a Fileless Attack?
In fileless attacks, malicious actors infiltrate, seize control, and conduct malicious activities by taking advantage of vulnerable software that an end user might routinely employ, such as Microsoft Word or the Chrome browser or software already installed on a server.
These actors can also exploit vulnerabilities to access native operating system utilities like PowerShell or any application that grants high-level access and privileges. These utilities allow actors to execute fundamental commands across a network. Fileless attacks frequently arise because conventional antivirus (AV) software is not designed to identify and thwart non-malware assaults. Consequently, malicious actors can exploit a fileless attack as a means of entry that may go entirely unnoticed unless more sophisticated security measures are implemented.
Disabling Default Command Line Rules
If this setting is enabled, SecureAge Central will send the default list to the end user. If the setting is disabled, SecureAge Central will not send the default list.
To disable Default Command Line Rules
-
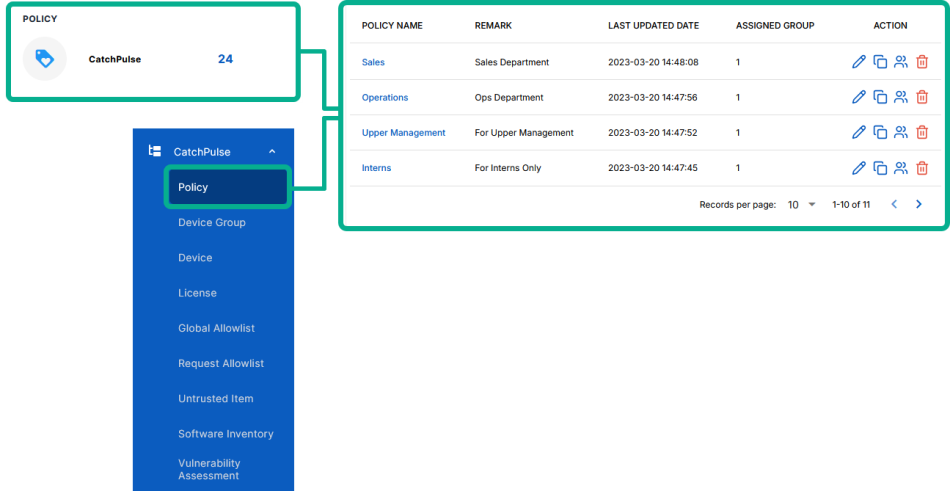
From the main navigation bar, go to CatchPulse → Policy.
-
Do one of the following:
-
To create a new policy and disable default command line rules, click on the Add Policy button located at the top right corner of the Policy page, or
-
To disable a default command line rules to an existing policy, select a policy and click on the corresponding
 button.
button.
-
-
On the Policy page, under Manage → Command Line Rules.
-
Turn off Use Default Command Line Rules switch.
Adding multiple rules with varying parameters to the same process
If the default command line rules listed are not sufficient, or if additional measures can be implemented to protect against fileless attacks, you may create variations of these rules.
This is a precautionary measure for enhanced security. Consider adding multiple rules with different parameters for the same process. This approach will help ensure that the processes' rules, parameters, and actions are comprehensive and thorough.
-
From the main navigation bar, go to CatchPulse → Policy.

-
Do one of the following:
-
To create a new policy and add multiple rules with varying parameters to the same Command Line Rules process, click on the Add Policy button located in the top right corner of the Policy page, or
-
To add multiple rules with different parameters to the same Command Line Rules in an existing policy, select a policy and click on the corresponding
 button.
button.
-
-
On the Policy page, under Manage → Command Line Rules.
-
Select a Command Line Rules and click on the corresponding
 button.
button. -
On the Add Command Line Rules display box, add rules with varying parameters to the same process.
-
Process
Specify the name of the executable or process for which you want to set rules. This could be any program that can be executed from the command line.
-
Parameters
- Rules - This drop down allows you to select the type of match that should be applied to the command-line parameters, such as an exact match, starts with, or contains.
- Case Sensitive - Choose whether the parameter matching should be case sensitive.
- Parameter - Enter the specific command-line parameters you want to create a rule for.
-
Process Action
From the drop down menu, select the action to take when the specified process and parameters are encountered.
You have three options: always block, allow a trusted user to decide, or never trust permanently.
-
-
(Optional) Select Add another to continue adding Command Line Rule.
-
Select Add to add a Command Line Rules.
You will be directed to the User-Defined Command Line Rules tab, and the notification panel at the bottom of the page will indicate that the Command Line Rules have been added.
Adding New User-Defined Command Line Rules
To add New User-Defined Command Line Rules
-
From the main navigation bar, go to CatchPulse → Policy.

-
Do one of the following:
-
To create a new policy and add a new User-Defined Command Line Rule, click on the Add Policy button located at the top right corner of the Policy page, or
-
To add a new User-Defined Command Line Rule to an existing policy, select a policy and click on the corresponding
 button.
button.
-
-
On the Policy page, under Manage → Command Line Rules.
-
Click Add New User-Defined from the top right corner of the Command Line Rules page.
-
On the Add Command Line Rules display box, create command-line rules that are not part of the default set provided by the system.
-
Process
Specify the name of the executable or process for which you want to set rules. This could be any program that can be executed from the command line.
-
Parameters
- Rules - This drop down allows you to select the type of match that should be applied to the command-line parameters, such as an exact match, starts with, or contains.
- Case Sensitive - Choose whether the parameter matching should be case sensitive.
- Parameter - Enter the specific command-line parameters you want to create a rule for.
-
Process Action
From the drop down menu, select the action to take when the specified process and parameters are encountered.
You have three options: always block, allow a trusted user to decide, or never trust permanently.
ACTION EXPLANATION PROMPTS Always block:
Never trust the command line that matches the rules. This will simply always block it
Let Trusted user decide, where: (a) For users who are in the trusted account list and in Interactive Mode, CatchPulse Application Allowlisting will prompt for the possible actions: Unblock & Trust, Continue Blocking, Trust Once.
i) Unblock and Trust – The command line will be unblocked and executed. CatchPulse will automatically add the command line into the allowlist database (Manage → Application Control → Allowed Commands
ii) Continue Blocking - The command line will be blocked
iii) Trust Once - The command line will only be trusted once.
(b) For non-trusted account users who will be in Lockdown Mode, the default action is to never trust the command line and will always block it. (c) In Trust All mode, the command line will be automatically trusted permanently. CatchPulse will automatically add the command line into the allowlist database (App Setting → Application Allowlisting → Command Line Settings → Allowlisted Command Line). Never trust permanently: (a) For the user in Interactive Mode & Trust All Mode, CatchPulse Application Allowlisting will prompt for the possible actions: Continue Blocking & Trust Once.
i) Continue Blocking - The command line will be blocked
ii) Trust Once - The command line will only be trusted once.
(b) For the user in Lockdown Mode, the default action is to never trust the command line and will always block it
-
-
(Optional) Select Add another to continue adding Command Line Rule.
-
Select Add to add a Command Line Rules.
The notification panel at the bottom of the page indicates the Command Line Rules was added.
Deleting a Command Line Rule
To delete a Command Line Rule
-
From the main navigation bar, go to CatchPulse → Policy.

-
Select a policy and click on the corresponding
 button.
button. -
On the Policy page, under Manage → Command Line Rules → User-Defined Command Line Rules tab.
-
Select a User-Defined Command Line Rule and click on the corresponding
 button.
button. -
When prompted to confirm deleting a Command Line Rule, choose Delete.
The Command Line Rule you selected has been deleted, as indicated in the notification panel at the bottom of the page.
More information
Support and feedback
Should you encounter any issues using the SecureAge Central with any of the mentioned or missed requirements above, you can always write to us a docs@secureage.com.
This page was last updated: September 09, 2025
